WELCOME
EXPOSED:
The Security Vulnerabilities Hackers See
That You Don't!
Discover Your Company's Exposure
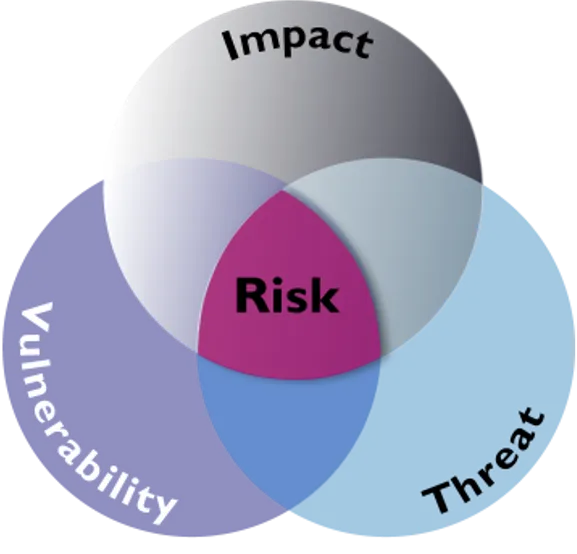
In today's rapidly evolving business landscape, your cybersecurity posture isn't what you think it is—it's what hackers can prove it is. While you focus on compliance checkboxes, cybercriminals are methodically probing your defenses, finding weaknesses your IT team missed, and preparing to breach systems you thought were secure.
Why Choose Elliptic Systems Corporation?
We Will Bring You To The Next Level Of Business Innovation

MILITARY-GRADE EXPERTISE: Our veteran-led team brings battle-tested precision and 30+ years of specialized security experience to identify what standard IT teams miss
PROACTIVE PROTECTION: While others wait for breaches to happen, we simulate sophisticated attacks to find vulnerabilities before real hackers exploit them
BLIND SPOT ELIMINATION: We uncover the hidden security gaps your team doesn't see—from overlooked multifactor authentication to dangerous web access vulnerabilities
BUSINESS-FOCUSED RESULTS: Our easy-to-understand reports translate technical vulnerabilities into business risk with clear, prioritized remediation steps
PROVEN METHODOLOGY: Our four-step assessment process delivers actionable insights in just two business days without disrupting your operations
The Anatomy of Our
IT Security Penetration Test

Previous Breach Vulnerability Assessment
Have you experienced a breach before? Lightning doesn't strike twice, but hackers do. We identify if attackers left backdoors in your systems and determine if you're still on their target list. 91% of organizations get attacked again after their first breach—we make sure you're not one of them.

Authentication and Access Control Testing
Can you access critical systems without multifactor authentication? We evaluate your authentication practices and validate that proper access tokens are required for all sensitive systems. Many breaches occur because this simple security measure is missing or misconfigured.

Phishing Resistance Evaluation
With 91% of cyberattacks starting with phishing emails and 1 in 5 employees clicking malicious links, your human firewall needs testing. We conduct controlled phishing simulations to identify vulnerable team members and provide targeted training to strengthen your weakest link.

Endpoint Security Analysis
Are your systems bombarded with pop-ups or warning messages? These are often signs you've already been compromised. We analyze your endpoint protection capabilities to ensure you have more than just basic antivirus protecting your devices from sophisticated modern threats.

Web Content Filtering Assessment
Can employees visit any website without restrictions? We test your web filtering solutions to ensure malicious sites are properly blocked. Unrestricted web access is a critical vulnerability, as research shows 1 in 5 employees will click malicious links without proper safeguards.

Security Architecture Review
Many organizations believe cloud storage means automatic security or that backups alone will save them from ransomware. We evaluate your entire security architecture to identify misconfigurations and blind spots in your defense strategy that could lead to catastrophic breaches.
Industries We Serve

Legal Industry
Transforming Legal Protection
Prevent unauthorized access to confidential client communications protected by attorney-client privilege
Ensure compliance with bar association data security requirements and ethical obligations
Protect sensitive case strategy documents from competitors or opposing counsel
Secure e-discovery platforms and document management systems from unauthorized access
Validate security of client portal systems where sensitive documents are exchanged
Identify vulnerabilities in time-tracking and billing systems that contain financial data
Prevent data breaches that could result in malpractice claims or reputation damage
Test security of remote work environments used by partners and associates
Assess third-party vendor security when using external services for document processing
Verify security controls protecting merger/acquisition data and other market-sensitive information

Healthcare Industry
Revolutionizing Healthcare Security
Validate HIPAA compliance with thorough testing of ePHI storage and transmission security
Secure electronic medical record (EMR) systems against unauthorized access or modification
Test security of telehealth platforms to ensure patient confidentiality during remote consultations
Identify vulnerabilities in connected medical devices that could impact patient safety
Verify segmentation between clinical and administrative networks for proper access control
Assess security of patient portals where sensitive health information is accessible
Test pharmacy management systems and prescription processing for security vulnerabilities
Validate proper access controls for different staff roles within healthcare information systems
Secure medical imaging systems (PACS) that contain sensitive diagnostic information
Identify potential weaknesses in health information exchanges with partner organizations

CPA Industry
Securing Accounting Solutions
Secure client financial data including tax returns, financial statements, and planning documents
Test security of tax preparation software and client data transmission mechanisms
Validate segregation of duties within accounting systems to prevent fraud
Identify vulnerabilities in client portals used for document exchange and signatures
Assess security of audit workpapers and client evidence documentation systems
Test access controls to prevent unauthorized disclosure of confidential financial information
Verify security of time and billing systems containing sensitive client engagement details
Assess security of cloud-based accounting platforms used for client services
Test security of business valuation data and other proprietary financial analyses
Identify vulnerabilities that could lead to unauthorized access of trust accounts or client funds

Achitecture & Engineering
Industry
Protecting Visionary Insights
Secure intellectual property including proprietary designs, blueprints, and specifications
Test security of CAD/BIM systems containing valuable project designs and client information
Assess security of project management platforms with sensitive timeline and budget data
Verify security of file-sharing systems used for large design file collaboration
Test access controls for different project teams to ensure appropriate separation
Validate security of building control system designs before implementation
Identify vulnerabilities in rendering farms or computational design systems
Assess security of client communications regarding sensitive project details
Test security of bid management systems containing competitive pricing information
Verify that proprietary engineering calculations and methods remain confidential

Construction Industry
Industrializing Security
Secure bid information and proprietary estimating data from competitors
Test security of project management systems containing schedules and resource allocations
Validate security of financial systems managing multi-million dollar project budgets
Assess vulnerability of building information modeling (BIM) data and design specifications
Verify security of subcontractor management systems and payment processing
Test security of equipment GPS tracking and asset management platforms
Identify vulnerabilities in site security systems for high-value construction locations
Assess security of contract management systems containing legally binding documents
Test access controls for sensitive drawings and specifications during project execution
Verify security of systems handling regulatory compliance documentation and permits

Finance Industry
Maximizing Financial Security
Validate compliance with strict regulatory requirements including SOX, GLBA, and PCI-DSS
Test security of online banking platforms and transaction processing systems
Secure customer financial data including account numbers, balances, and transaction history
Assess anti-fraud systems and detect potential bypass methods before criminals do
Verify security of investment management platforms handling high-value transactions
Test security of credit application processing and identity verification systems
Identify vulnerabilities in wealth management platforms containing comprehensive client data
Assess security of loan origination systems and document management platforms
Test security of mobile banking applications and API interfaces for weaknesses
Verify security controls protecting wire transfer systems and payment processors
Are You Just Dumping Money Into a Cybersecurity Bonfire? Find Out Now!
Don't let your competition get ahead in the AI race. Schedule a free consultation with our experts to discover how Elliptic Systems Corporation can help you harness the power of AI to drive growth and innovation.
Hear it from our Clients

Elliptic Systems is always presenting and implementing best practices. They take a proactive stance when it comes to our data and network, treating it as if it were their own. They have implemented advanced systems, keeping us safe and protected. They work around our schedule to minimize the amount of disruption to our business and workflow.
Sabrina Layman
Managing Partner - Attorney
Brewe Layman, P.S.
‘VOTED BEST LAWYERS’

Every company needs a roadmap on how to navigate the complex world of business issues that can affect and hold your company back. Eric is an industry veteran who has a wealth of knowledge. I highly recommend you don't miss this opportunity to work with Elliptic Systems.
Nathan Ware
President
Rain Networks
Office: Seattle, WA
Office: Phoenix, AZ
Office: Hawaii
Call 425-441-9500
Call 480-207-7979
Call 808-883-3222
Email: [email protected]
Site: www.ellipticsystems.com
